Active directory security
Active directory is quickly becoming a critical failure point in any big sized company, as it is both complex and costly to secure...
With the default license, the binary program can be run for free, as long as you do not derive any revenue from it. For example, any for-profit organizations can use it to audit their own systems.
DNSSEC adds two important features to the DNS protocol:
->Data origin authentication allows a resolver to cryptographically verify that the data it received actually came from the zone where it believes the data originated.
->Data integrity protection allows the resolver to know that the data hasn't been modified in transit since it was originally signed by the zone owner with the zone's private key.
DNS zone transfer vulnerability
A zone transfer that is from an external IP address is used as part of an attackers reconnaissance phase. Usually, a zone transfer is a normal operation between primary and secondary DNS servers in order to synchronise the records for a domain. This is typically not something you want to be externally accessible.
SPF and DMARC records
SPF checks whether an email really originates from your email servers. This prevents others from sending malicious emails in name of your organization.
domain.com TXT record "v=spf1 include:_spf.protonmail.ch mx -all"
DMARC tells your email server what to do when it receives an email that fails the SPF and DKIM checks and reports abuse to your organization.
_dmarc.domain.com TXT record "v=DMARC1; p=reject; rua=mailto:abuse@domain.com; ruf=mailto:abuse@domain.com; sp=none; fo=1; aspf=s; adkim=s; ri=86400"
DKIM record and STARTTLS and DANE
DKIM checks the identity of the sender and the integrity of the message. This prevents others from spoofing or manipulating your emails.
domain.com TXT record "v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA4TWhAkE9cQBB7g2C6jGb...."
STARTTLS establishes a secure connection between email servers. DANE authenticates the receiving email server and guarantees the use of a secure connection with STARTTLS. DANE relies on DNSSEC for trust in the DNS entries.
DANE checker (SMTP)
DANE checker2 (SMTP, IMAP, POP3)
WEB security
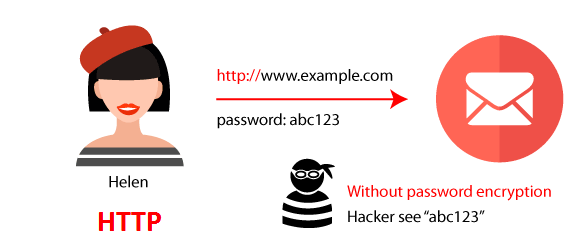
HTTP (HyperText Transfer Protocol)
HTTP is an application layer protocol for information systems.
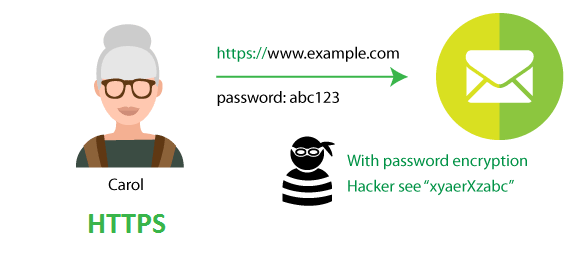
HTTPs (HyperText Transfer Protocol secure)
HTTPs is used for secure communication over a network. Communication protocol using encryption protocol TLS v1.1 or v1.2. HTTPs ensures protection of the privacy and integrity of the exchanged data in transit.
Network security
Network Access Control (NAC) helps enterprises implement policies for controlling devices and user access to their networks. NAC can set policies for resource, role, device and location-based access and enforce security compliance with security and patch management policies, among other controls.
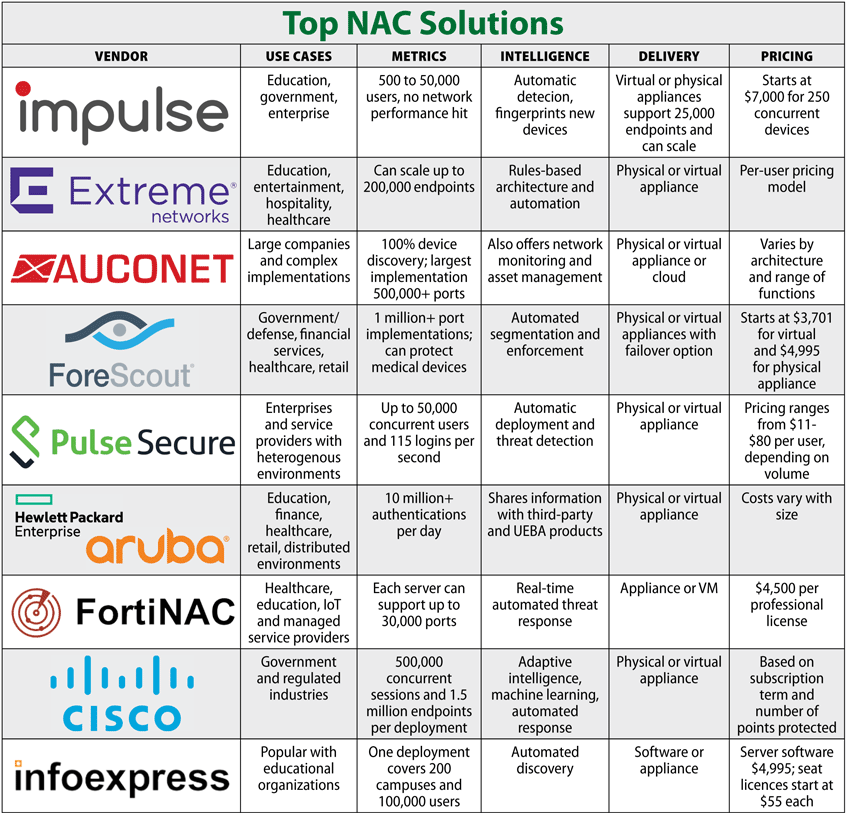
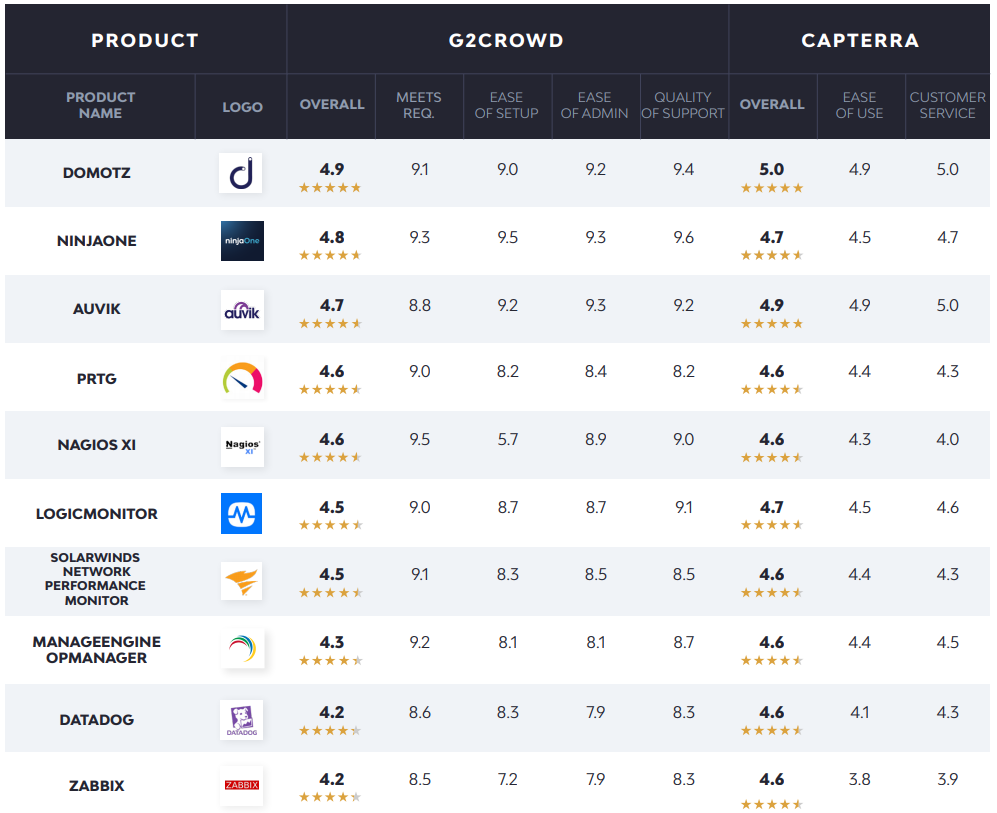
Network monitoring
The following solutions provide additional visibility and management over SNMP devices (routers, switches, firewalls, printers, IoT devices, etc.) and more.
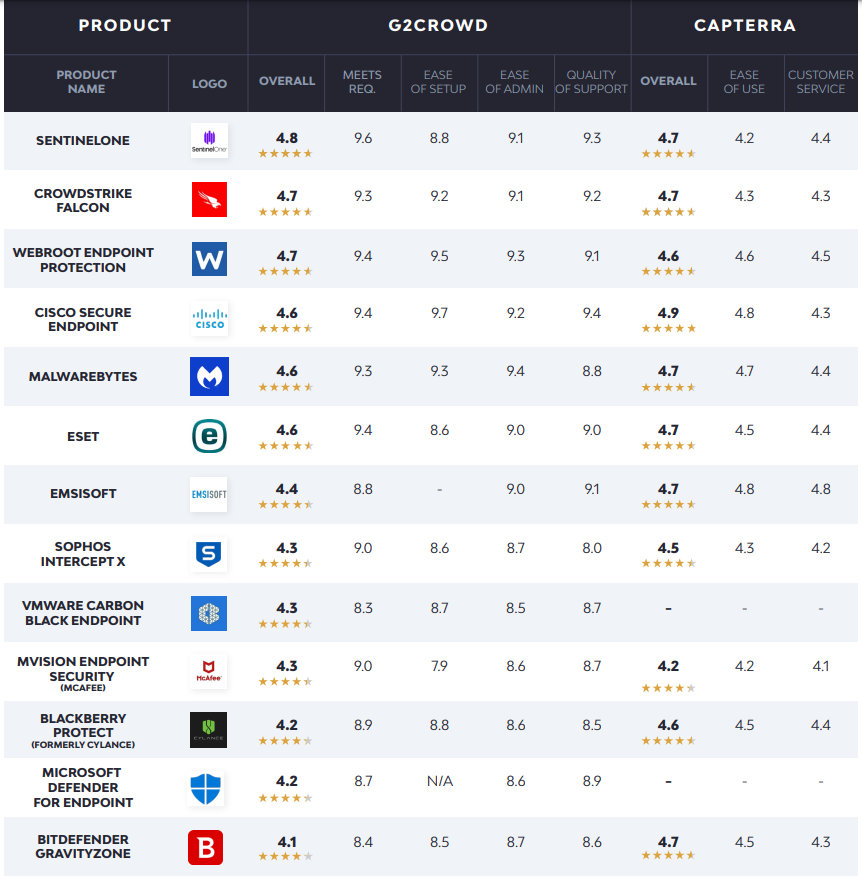
Endpoints security, management, monitoring
Endpoints security
The endpoint security landscape is crowded and constantly in flux. To keep things simple, we’ve narrowed this list to endpoint protection products.
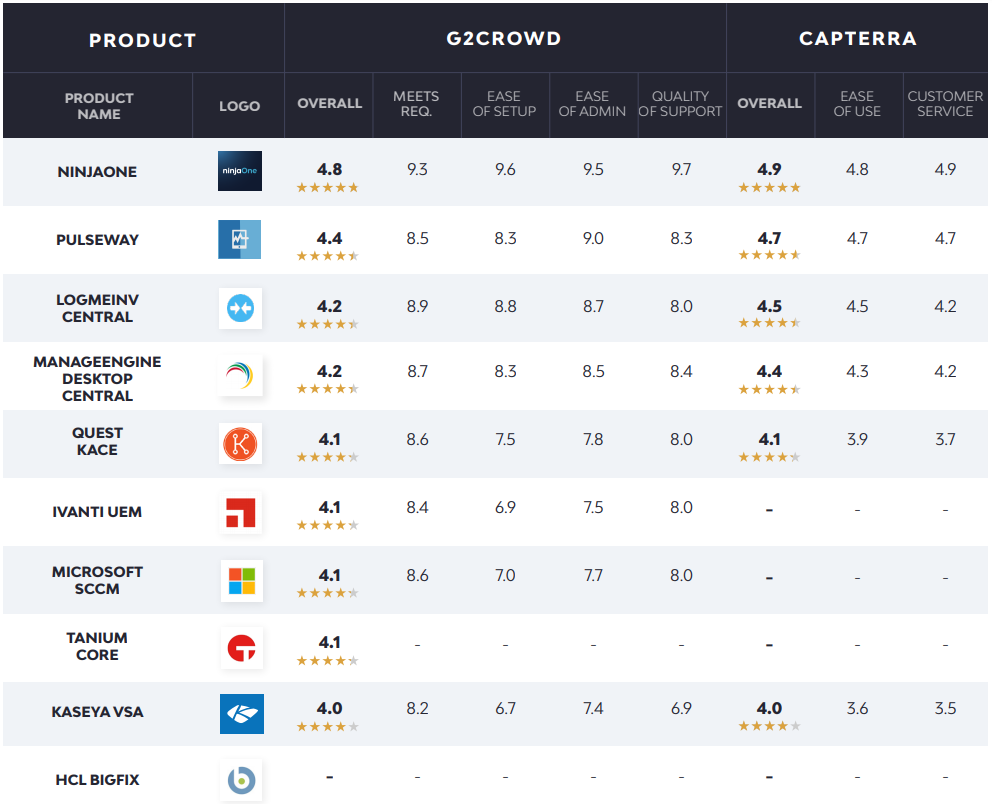
Endpoints management and monitoring
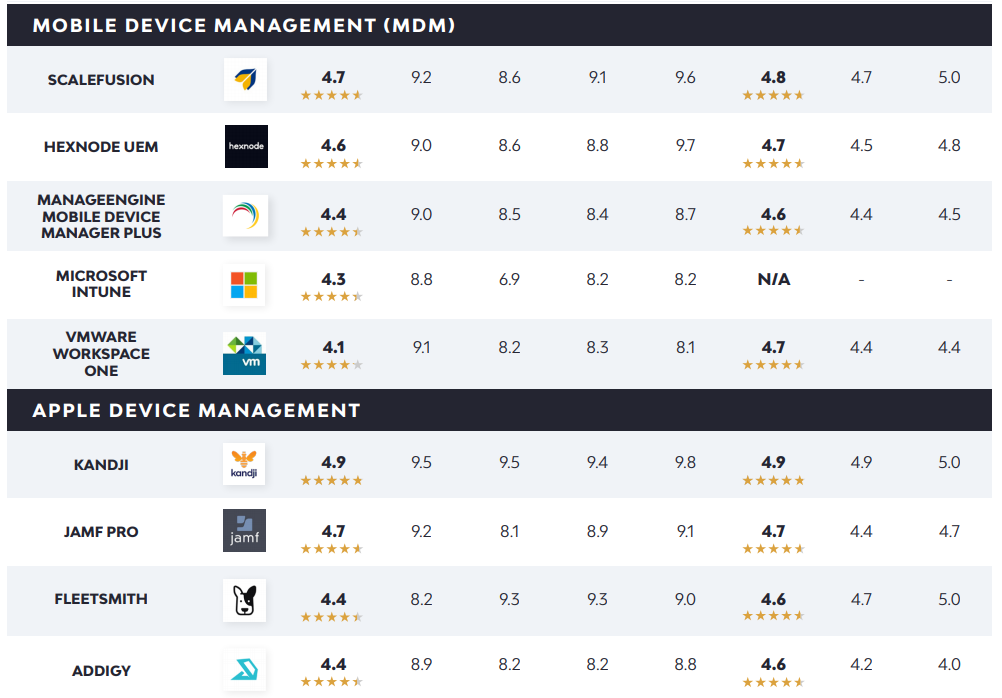
With many admins now responsible for managing an increasingly complex variety of systems and devices, the ability to centrally manage them all has become a core requirement for modern IT administration. The following are the highest-ranked endpoint management tools, with MDM solutions and tools designed specifically for Apple devices ranked in their own subgroups.
Software patch management
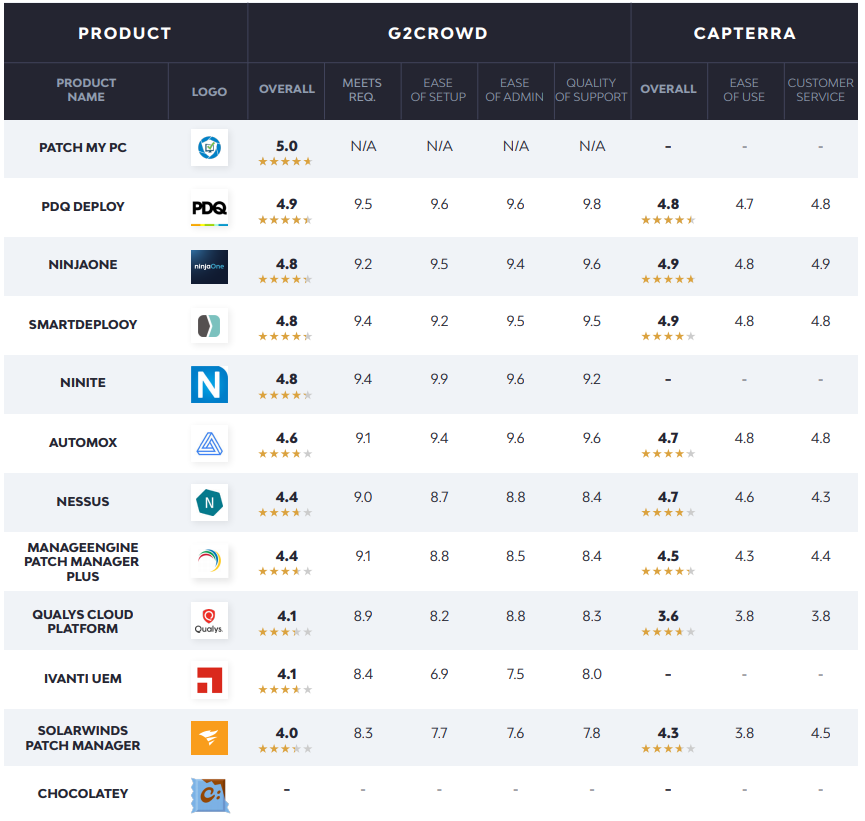
Keeping operating systems and 3rd-party applications patched and protected against the latest vulnerabilities is a critical but time-consuming responsibility. These solutions automate the process, and can help admins deploy and uninstall applications, as well.
IT asset management
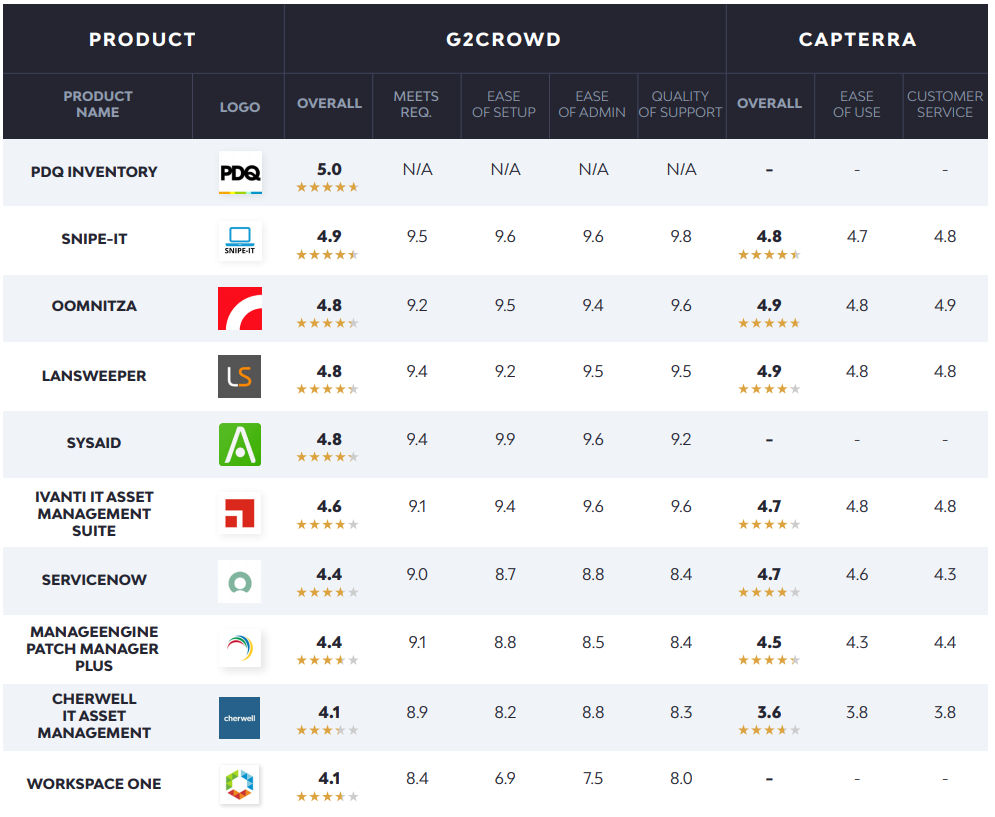
You can’t secure or manage what you can’t see. That’s why it’s important for admins to leverage software that can discover, track, and provide real-time insights on all their IT assets.
Information security
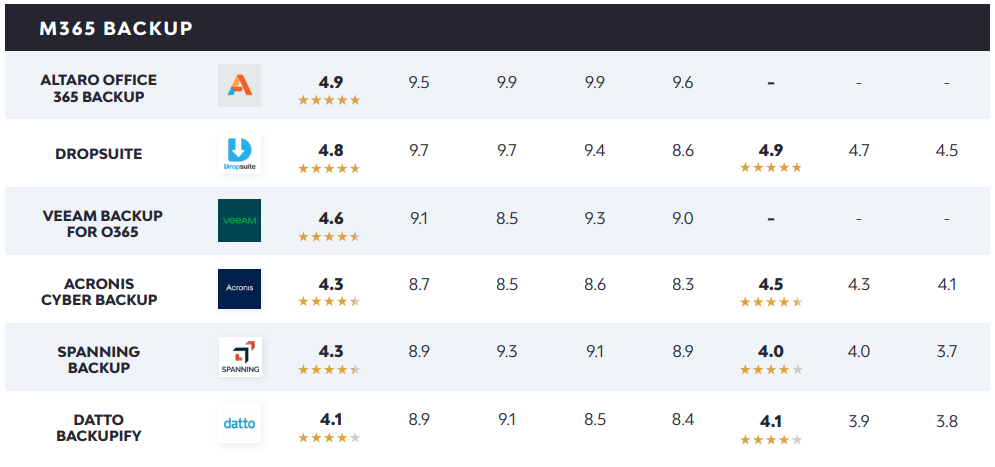
Backup management
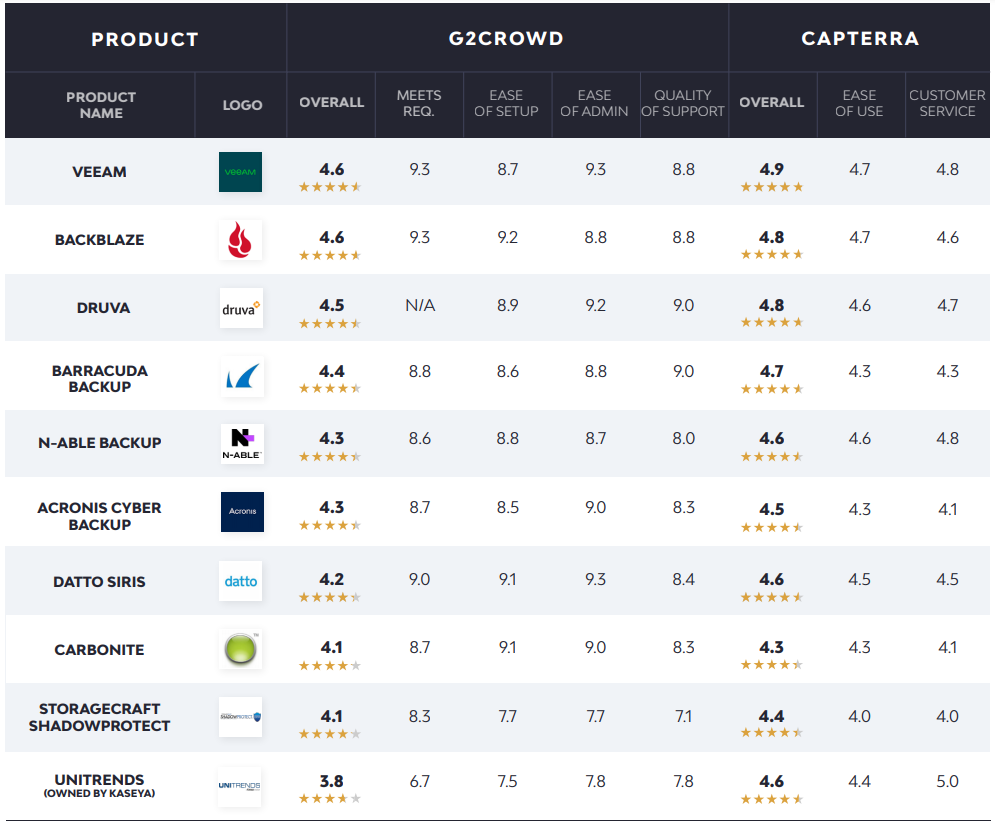
Properly managing backup solutions has become another core IT priority, especially with the rise of ransomware and other destructive online threats. The following list focuses on cloud-based backup solutions, with a subsection for M365 backup tools.
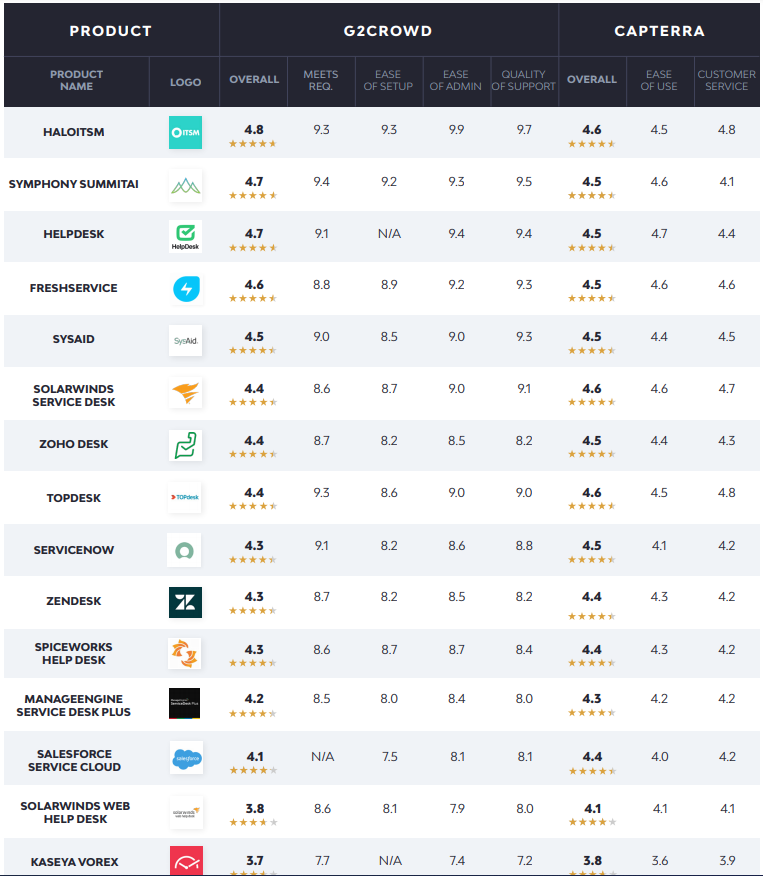
Service desk
The right service desk software can save IT technicians time and result in improved end-user experiences.
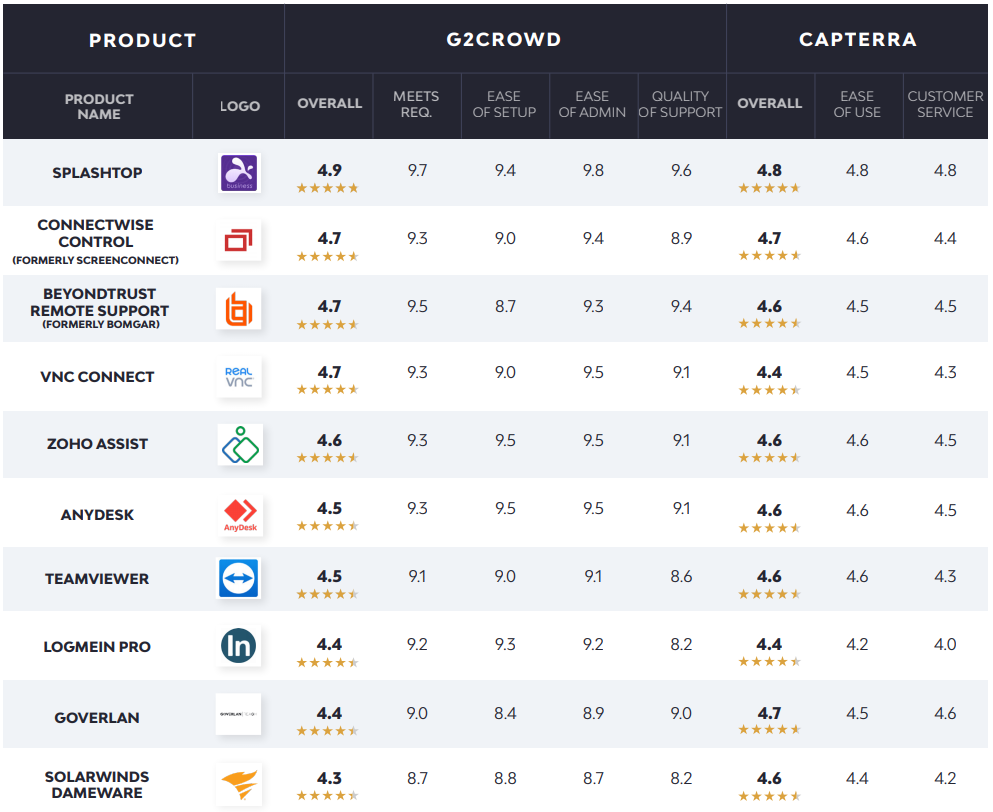
Remote desktop
Remote desktop solutions play a critical role in modern IT management, offering admins the ability to gain quick and reliable remote access to machines for hands-on troubleshooting and more.
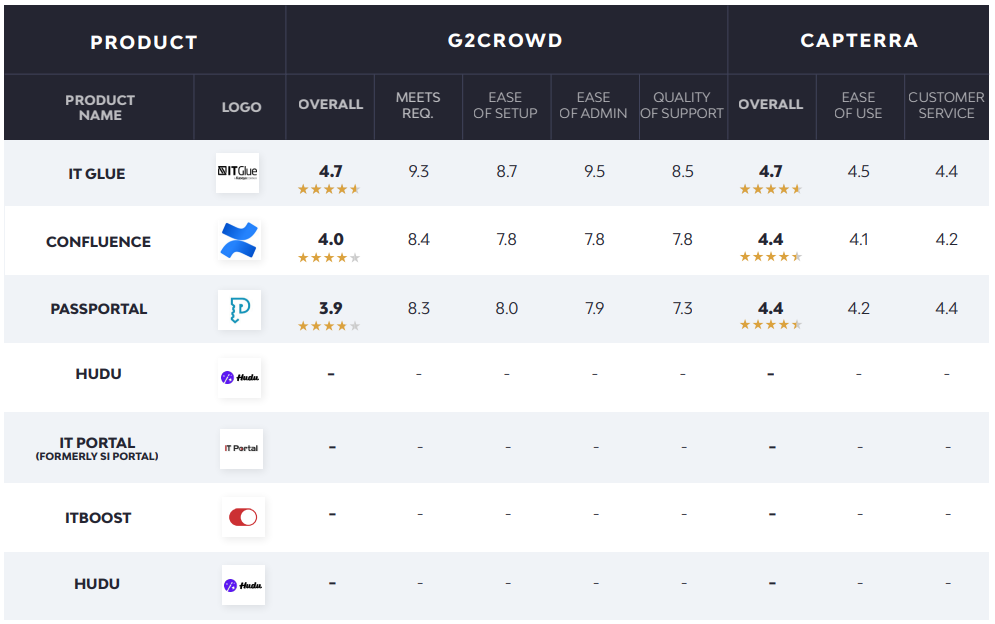
IT documentation
Good documentation is the key to better, faster, and scalable support. The following solutions aim to give admins the information they need, exactly where and when they need it.